 Blog Post
Blog Post
Securing the Software Supply Chain: How RESCALE’s Static Code…
Modern software supply chains rely on numerous third-party components, open-source dependencies and in-house codebases. This complexity introduces significant security risks, as vulnerabilities can emerge at any stage of software development. Static code analysis serves as an essential first line of defense, identifying security flaws early, long before code is executed. Within the RESCALE project, the Static Code Analysis Module plays a pivotal role in safeguarding software supply chains by analyzing code for vulnerabilities and ensuring compliance with security standards.
The Static Code Analysis Module is a key component of RESCALE’s broader security framework. It is designed to automate and standardize the detection of security flaws at the source code level, making it an integral part of the supply chain security assurance process. This module is responsible for assessing software artifacts before they move forward in the supply chain, ensuring that each component is verified, documented, and assigned a security guarantee based on its analysis.
How the Static Code Analysis Module Works
The architecture of the Static Code Analysis Module is structured to efficiently process source code using multiple analysis techniques. The module integrates several static analysis tools, each contributing insights into different aspects of software security. The results from these tools are then aggregated into a comprehensive security report, ensuring that vulnerabilities are identified and properly categorized.
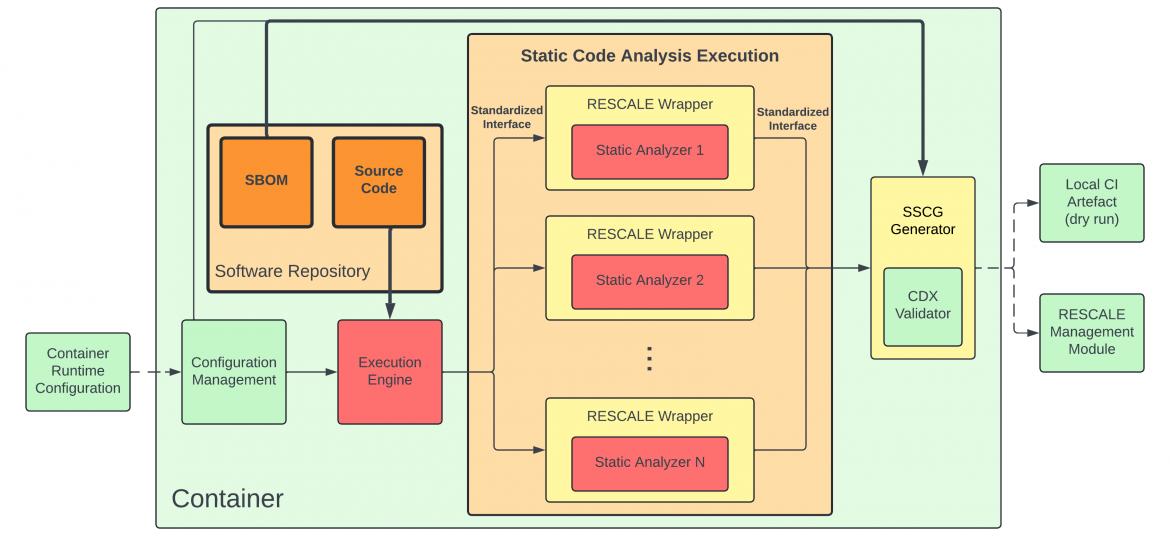
The Static Code Analysis Module operates within a containerized environment, ensuring consistency and reproducibility across different software projects. As shown in the diagram, the process begins with a software repository, where both source code and an SBOM (Software Bill of Materials) are stored. The Execution Engine manages the analysis workflow, sending the code through multiple static analyzers wrapped in a standardized RESCALE interface. These analyzers can vary depending on the language and security requirements of the project. Once the analysis is complete, the results are processed by the SSCG Generator, which validates the findings using the CDX Validator, ensuring that the final security report aligns with RESCALE’s structured security framework.
One of the module’s core outputs is the Static Supply Chain Component Guarantee (SSCG). This guarantee is a structured security assessment document generated from the results of static code analysis, serving as an assurance mechanism for software components. The SSCG provides a detailed breakdown of detected vulnerabilities, code quality issues, and compliance with security policies. Within the module, the SSCG is generated through a step-by-step workflow, where multiple analyzers contribute their findings, which are then processed into a unified security report.
The Static Code Analysis Module is designed to support a wide range of programming languages and analysis methodologies. By incorporating both traditional static analysis techniques and advanced verification methods, it offers a multi-layered security approach. This includes formal verification, which checks software behavior against predefined security models, and symbolic execution, which explores potential execution paths to uncover vulnerabilities that may not be detected by traditional methods.
The modular design of the Static Code Analysis Module ensures that new analysis tools can be integrated easily, allowing the module to evolve alongside emerging security threats. This adaptability is critical for maintaining long-term software supply chain security, as new vulnerabilities and attack techniques continue to emerge.
Integration with the RESCALE Framework
The Static Code Analysis Module is not an isolated tool; it functions as a key part of the RESCALE security pipeline. It integrates with other security testing components, including dynamic analysis and low-level security testing, ensuring that software is evaluated from multiple perspectives before deployment. The results from static analysis feed into the broader security assessment process, allowing organizations to track security findings across the entire supply chain lifecycle.
Another major advantage of this module is its ability to automate security testing within CI/CD workflows. By embedding static analysis directly into software development pipelines, it ensures that every code update is automatically scanned for security issues before being merged or deployed. This continuous security approach reduces the likelihood of vulnerabilities reaching production, significantly lowering the risk of software supply chain attacks.
Why Static Code Analysis Matters for Supply Chain Security
Static code analysis is particularly valuable for securing third-party dependencies and open-source components, which are often integrated without full visibility into their internal security. By rigorously analyzing source code, the Static Code Analysis Module helps organizations detect insecure coding practices, misconfigurations, and hidden vulnerabilities before they can be exploited.
Beyond just detecting issues, the SSCG produced by the module provides a traceable security guarantee, allowing organizations to assess the trustworthiness of software components before integration. This aligns with RESCALE’s overarching goal of building a Trusted Bill of Materials (TBOM), which consolidates security guarantees across the entire supply chain. However, while the SSCG is a foundational component, the TBOM itself will be covered separately in another article to maintain a clear focus on the architecture and function of the Static Code Analysis Module.
Conclusion
The Static Code Analysis Module in RESCALE is a crucial element in securing software supply chains. By leveraging multiple analyzers, formal verification, and symbolic execution, it provides a rigorous security assessment for software components. The SSCG provides a structured security assessment for each component, helping organizations assess risks and ensure compliance.
In the next article, we will explore the specific tools powering this module, including SAVE-ME, SASTer, and IVEE, and examine how they enhance vulnerability detection in modern software ecosystems.