 Blog Post
Blog Post
The Tools Powering RESCALE’s Dynamic Testing Module
Ensuring the security of modern software requires more than just static analysis. Many vulnerabilities only emerge at runtime, making dynamic testing essential for detecting issues related to input validation, execution misconfigurations, and API security flaws. The Dynamic Testing Module in RESCALE integrates multiple specialized tools that execute software in controlled environments, providing a comprehensive assessment of software security before deployment. Each tool plays a distinct role in detecting different types of vulnerabilities, allowing for a multi-layered approach to security testing.
FATex: Fault Tolerance and Resilience Testing
FATex is designed to analyze how software behaves under fault conditions, focusing on the resilience of compiled applications. It introduces simulated failures and stress conditions, identifying points where an application may crash, behave unpredictably, or expose security risks. Unlike traditional fuzzers, FATex does not focus solely on input mutation but evaluates how execution paths respond to failures. This allows security teams to assess exception handling mechanisms, error recovery strategies, and overall system stability. By identifying weak points in an application’s fault tolerance, FATex helps developers build more robust and secure software.
RAISE: API Security Testing with ML-Driven Fuzzing
RAISE is a dynamic API security testing tool that automates the evaluation of web services, ensuring that API endpoints are resistant to attacks. Many modern applications rely on RESTful APIs, making API security a crucial aspect of software assurance. RAISE integrates with RESTler, a security-focused API fuzzer that generates API test cases using a grammar-based approach. By leveraging machine learning and genetic algorithms, RAISE optimizes the fuzzing process, identifying API vulnerabilities such as authentication bypasses, unauthorized access risks, and improper input validation. The tool systematically explores API execution paths, learning from previous test results to refine its approach and improve vulnerability detection.
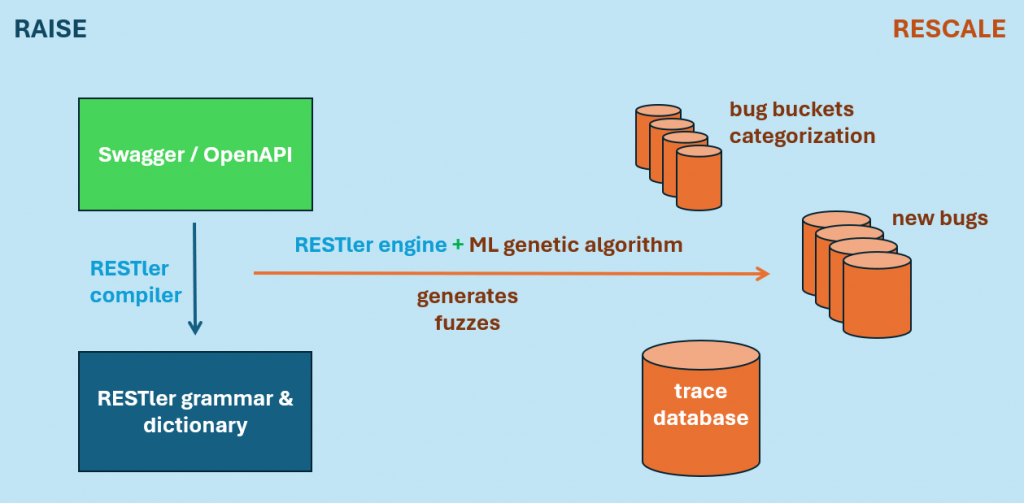
The provided diagram illustrates how RAISE integrates with RESTler. The system starts with an OpenAPI or Swagger specification, which is compiled into an API grammar. The RESTler engine, enhanced with machine learning, generates fuzzing test cases designed to trigger security flaws. The results are stored in a trace database, where they are categorized into bug buckets for further analysis. This structured approach ensures that API vulnerabilities are identified efficiently and that the results are documented in a way that aids remediation efforts.
EvoMaster: AI-Driven Automated Test Case Generation
EvoMaster is designed to automate test case generation using evolutionary algorithms. Traditional testing relies on manually crafted test cases, which can be time-consuming and limited in coverage. EvoMaster generates test cases dynamically by leveraging OpenAPI schemas, systematically exploring execution paths, and identifying vulnerabilities through an AI-driven mutation-based approach. This method increases the likelihood of detecting hidden security flaws, particularly in applications with complex input handling.
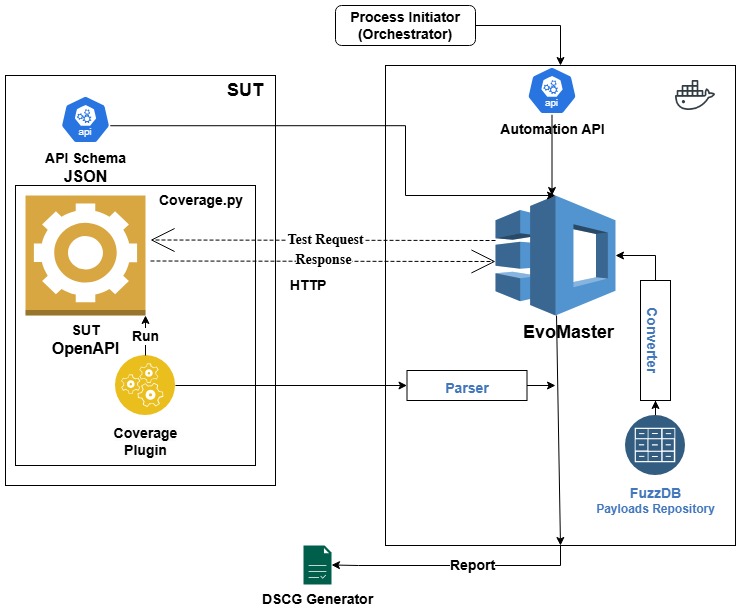
The EvoMaster workflow diagram demonstrates how the tool interacts with a system under test (SUT). An API schema in OpenAPI format defines the expected structure of the API. The coverage plugin monitors execution coverage, helping EvoMaster optimize its test case generation process. The tool sends test requests and analyzes responses, using data from FuzzDB, a repository of attack payloads, to detect security weaknesses. Results are parsed and aggregated, contributing to the security assessment of the tested system. The final test report is generated and incorporated into the Dynamic Supply Chain Component Guarantee (DSCG), ensuring that all findings are properly documented.
Standardizing Security Findings with DSCG
The results from FATex, RAISE, and EvoMaster are aggregated into the Dynamic Supply Chain Component Guarantee (DSCG), a structured document that consolidates security assessment findings from dynamic testing. The DSCG ensures that runtime security evaluations are standardized and traceable, providing a detailed breakdown of vulnerabilities, risk assessments, and compliance with security policies.
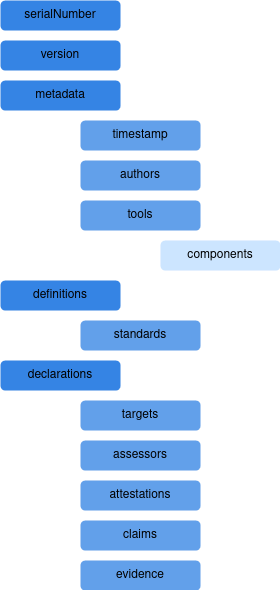
The DSCG structure, as shown in the provided diagram, includes metadata such as the serial number, version, and tool information. It also contains declarations specifying security targets, claims, and evidence gathered during testing. Definitions and standards are incorporated to align the findings with established security frameworks. The CDX Validator processes the DSCG, ensuring that the results conform to industry standards before they are sent to the RESCALE Management Module. This guarantees that security assessments from dynamic testing contribute directly to the broader supply chain security framework.
Conclusion
The Dynamic Testing Module in RESCALE integrates multiple specialized tools to detect vulnerabilities that only emerge at runtime. FATex ensures that applications are resilient against faults and execution failures. RAISE systematically tests API security, using machine learning-driven fuzzing to uncover authentication and authorization flaws. EvoMaster automates test case generation, leveraging evolutionary algorithms to identify security risks in software execution paths. Together, these tools provide a comprehensive runtime security assessment, strengthening the security posture of software components before deployment.
Through the DSCG, the results of these security evaluations are standardized, validated, and integrated into the RESCALE security framework. As cyber threats evolve, dynamic testing plays a critical role in securing modern applications, ensuring that vulnerabilities are detected and mitigated before they can be exploited.