 Blog Post
Blog Post
Detecting Hardware Vulnerabilities: The Role of RESCALE’s Dynamic Hardware…
As modern computing systems become more interconnected, the need for hardware-level security has never been more critical. While traditional security measures focus on software vulnerabilities, attackers increasingly exploit low-level hardware flaws to bypass security protections, extract sensitive information, or launch side-channel attacks. Hardware vulnerabilities are particularly dangerous because they often persist across software updates and may not be easily patched once a system is deployed.
Within the RESCALE project, the Dynamic Hardware Analyzer is specifically designed to address these risks by detecting and analyzing hardware vulnerabilities and leakage threats. By employing advanced security testing techniques, the module helps uncover side-channel attack (SCA) risks, power analysis vulnerabilities, and data leakage threats in cryptographic and FPGA-based systems
Understanding Hardware Vulnerabilities and Side-Channel Attacks
Hardware vulnerabilities can arise due to various factors, including design flaws, unintended electromagnetic emissions, power fluctuations, or signal timing variations. Unlike software-based vulnerabilities, these issues cannot be fixed with a simple patch; instead, they require thorough detection and mitigation strategies before deployment.
One of the most concerning classes of hardware threats is side-channel attacks. These attacks do not directly exploit software bugs but rather take advantage of unintended physical leakages such as power consumption, electromagnetic emissions, or execution timing. SCAs are particularly effective against cryptographic hardware implementations, allowing attackers to extract secret encryption keys by analyzing physical behavior rather than breaking the encryption algorithm itself.
The Dynamic Hardware Analyzer in RESCALE is designed to systematically detect such vulnerabilities, ensuring that hardware security risks are identified before attackers can exploit them.
How the Dynamic Hardware Analyzer Works
The Dynamic Hardware Analyzer is an advanced security testing module that evaluates hardware components, cryptographic accelerators, and FPGA-based designs for security weaknesses. Its primary role is to collect, process, and analyze side-channel leakage traces, determining whether a system exhibits security flaws that could be exploited through power analysis, timing attacks, or other forms of SCAs.
The process begins with trace collection, where the analyzer captures physical side-channel data from hardware devices during cryptographic operations or other sensitive computations. Once collected, these traces undergo trace preprocessing, where signal processing techniques and statistical methods such as the Trace Preprocessing Software Library and SCA Script Software Library are applied to remove noise and extract useful security insights. Finally, the system conducts attack simulations and risk assessments, leveraging Test Vector Leakage Assessment (TVLA) tests and NS report-based analysis to determine whether an attacker could successfully exploit the detected leakages.
These steps ensure a comprehensive evaluation of hardware security risks, helping organizations strengthen their supply chain security before deploying critical hardware components.
Architecture of the Dynamic Hardware Analyzer
The architecture of the Dynamic Hardware Analyzer is structured to efficiently process side-channel leakage data and detect potential hardware vulnerabilities. It consists of several key components that work together to analyze security risks in cryptographic implementations and FPGA-based systems.
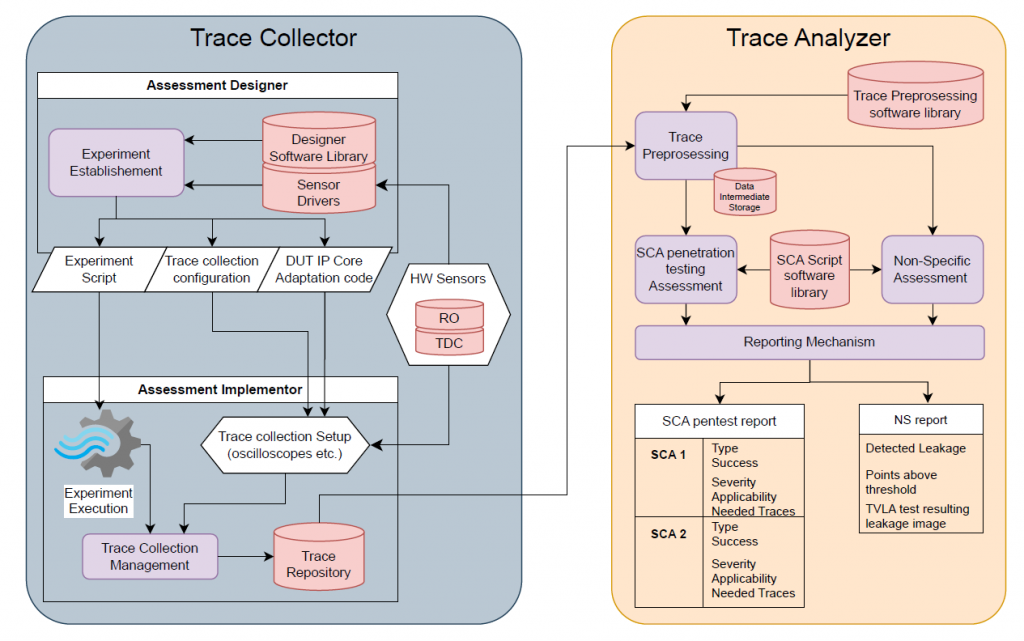
As illustrated in the Dynamic Hardware Analyzer architecture, the module consists of three main layers: the Trace Collection Layer, the Trace Analysis Layer, and the Evaluation and Reporting Layer. The Trace Collection Layer is responsible for capturing side-channel data such as power consumption, electromagnetic emissions, or execution timing variations from a target hardware system. This data is then transferred to the Trace Analysis Layer, where advanced statistical methods, correlation analysis, and machine learning models process the information, identifying whether the hardware leaks sensitive information. Finally, the Evaluation and Reporting Layer integrates these findings into structured security reports, ensuring that vulnerabilities are properly categorized and assessed.
This layered architecture ensures that security assessments are not only comprehensive but also scalable, allowing multiple hardware components to be evaluated within a controlled environment. By structuring the analysis process in a modular way, the Dynamic Hardware Analyzer can be adapted to different hardware platforms, making it a versatile tool in RESCALE.
Integration with RESCALE
The Dynamic Hardware Analyzer does not function in isolation. It is fully integrated into the broader RESCALE security pipeline, ensuring that hardware security risks are assessed alongside software vulnerabilities. The findings from the module contribute directly to RESCALE’s Trusted Bill of Materials (TBOM), consolidating security guarantees across the entire supply chain.
By working in conjunction with other security modules, such as the Static Code Analysis Module and the Low-Level Security Testing Module, the Dynamic Hardware Analyzer ensures that both hardware and software components undergo rigorous security validation before deployment. This multi-layered security approach strengthens the overall resilience of computing systems, helping organizations detect, analyze, and mitigate hardware security threats before they become a liability.
Importance of Hardware Security
Hardware vulnerabilities are becoming an increasingly attractive target for advanced persistent threats (APTs) and state-sponsored attacks. Unlike software exploits, which can often be mitigated through patches and updates, hardware flaws may persist throughout a device’s lifecycle, making early detection crucial.
By integrating hardware security testing into supply chain security practices, organizations can reduce the risk of data breaches, intellectual property theft, and cryptographic key extraction. The Dynamic Hardware Analyzer in RESCALE ensures that hardware vulnerabilities are systematically detected and addressed, reinforcing the security of critical computing infrastructure.
Conclusion
The Dynamic Hardware Analyzer in RESCALE is a key component in modern hardware security testing, providing organizations with the ability to detect, analyze, and mitigate hardware-level vulnerabilities before they can be exploited. By leveraging advanced trace collection, preprocessing, and side-channel attack detection techniques, the module plays a crucial role in strengthening supply chain security.
By integrating with the broader RESCALE security framework, the module ensures that low-level security assessments contribute to the overall supply chain security process. In the next article, we will explore the specific tools and methodologies used within the Dynamic Hardware Analyzer, including trace collection devices, machine learning-based SCA detection techniques, and advanced cryptographic leakage assessments.