Blog Post
Blog Post
Inside RESCALE’s Static Analysis Toolkit: SAVE-ME, SASTer and IVEE
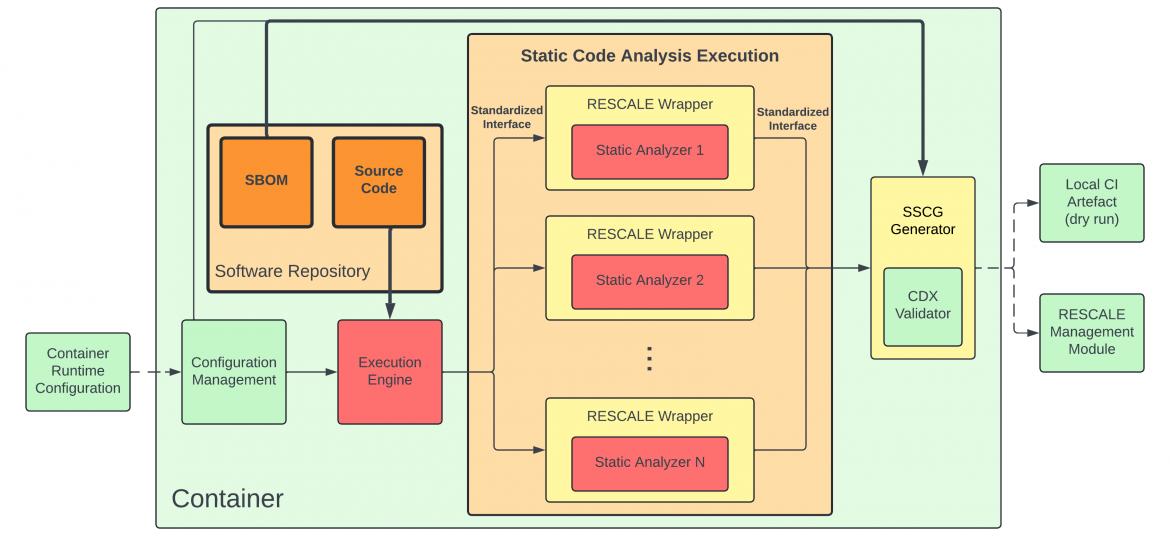
In modern software development, security vulnerabilities can emerge at any stage of the process, from initial coding to deployment. Detecting these vulnerabilities early is critical for maintaining a secure software supply chain. The Static Code Analysis Module in RESCALE incorporates multiple state-of-the-art analysis tools to ensure that software components are rigorously examined before they are integrated into a system. Three of the key tools driving this module’s capabilities are SAVE-ME, SASTer, and IVEE, each providing unique and complementary approaches to static vulnerability detection.
SAVE-ME: Leveraging Machine Learning for Vulnerability Detection
One of the most innovative tools within RESCALE’s static analysis toolkit is SAVE-ME, a system that integrates Machine Learning (ML) to enhance vulnerability detection in source code. SAVE-ME specifically targets Erlang code, using pre-trained transformer models to improve the accuracy of static analysis. Traditional static analysis tools often struggle with false positives and rule-based limitations, but SAVE-ME employs CodeBERT, a model trained on large-scale source code datasets, to detect vulnerabilities with higher precision.
The process begins with Erlang source code preprocessing, where functions are extracted and converted into tokenized representations using CodeBERT’s tokenizer, which has been adapted to handle Erlang-specific syntax. These tokens are then passed through pre-trained transformer layers, where the relationships between code elements are encoded. Finally, a fully connected neural network (classification head) analyzes the encoded data and produces an output with a confidence score, indicating whether a function is vulnerable or not.
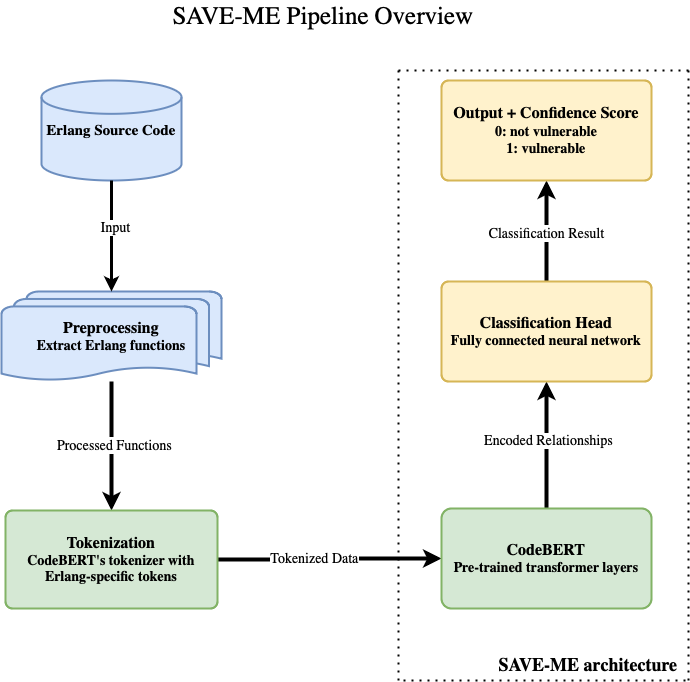
SAVE-ME’s ability to incorporate semantic understanding of source code, rather than relying solely on predefined rules, allows it to identify vulnerabilities that traditional static analysis tools might miss. This is particularly useful in large codebases, where manual security review is impractical, and dynamic testing is not always feasible.
SASTer: Multi-Language Static Analysis for Python and C/C++
While SAVE-ME focuses on ML-based vulnerability detection for Erlang, SASTer provides a broader static analysis framework designed to support Python and C/C++. It integrates multiple open-source static analyzers, including tools such as Bandit (for Python) and Semgrep (for flexible rule-based scanning).
SASTer is designed to standardize the output from multiple analyzers, ensuring that results are aggregated and normalized into a common security format. One of its key advantages is its ability to filter false positives intelligently, reducing the burden on security teams by prioritizing high-confidence findings.
IVEE: Symbolic Execution for Deeper Vulnerability Discovery
The Intelligent Vulnerabilities Exposure Engine (IVEE) enhances static analysis by incorporating symbolic execution, a technique that systematically explores possible execution paths within a program to identify hidden vulnerabilities. Unlike traditional static analyzers that primarily rely on pattern matching, IVEE can analyze complex code flows and detect vulnerabilities that manifest only under specific conditions.
By using symbolic execution, IVEE is particularly effective at detecting memory safety issues (such as buffer overflows) and logical errors that might not be apparent through conventional static analysis techniques. Within the Static Code Analysis Module, IVEE acts as a deep analysis layer, complementing both SAVE-ME and SASTer by identifying difficult-to-find vulnerabilities that evade rule-based or ML-based approaches.
How These Tools Contribute to SSCG
Each of these tools, SAVE-ME, SASTer, and IVEE, contributes to the Static Supply Chain Component Guarantee (SSCG) by generating detailed security assessments. The SSCG framework ensures that all vulnerabilities detected by these tools are properly documented and categorized, providing a clear security profile for each software component.
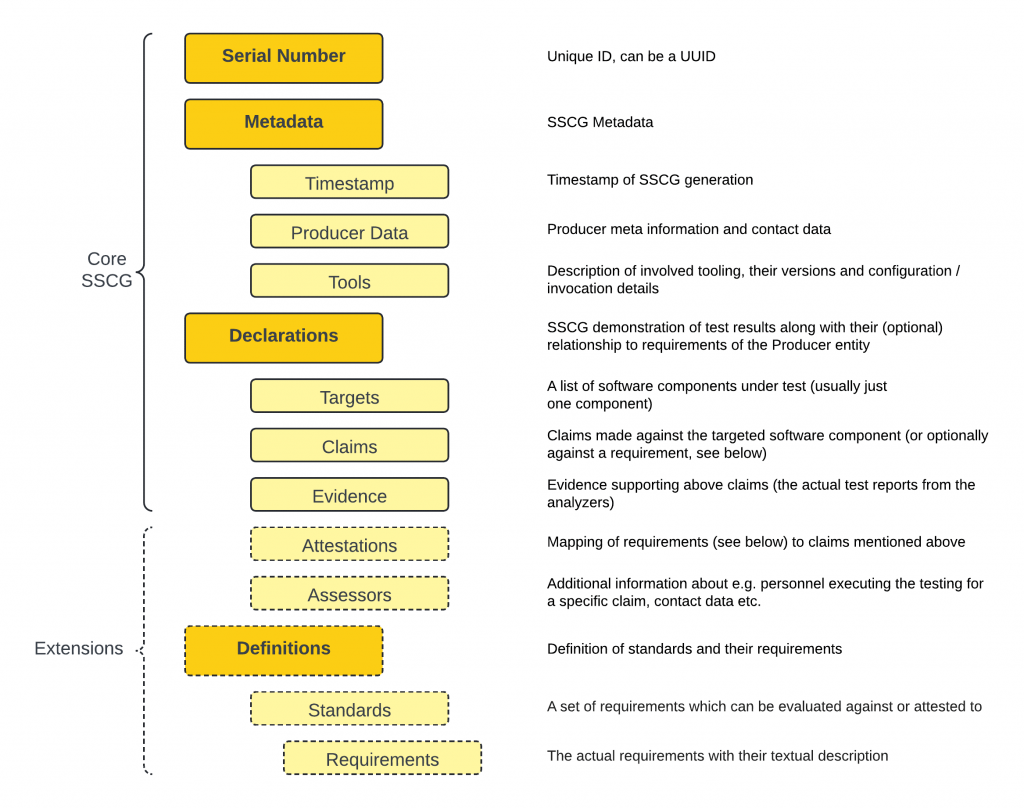
The SSCG structure includes metadata about the tools used, their configuration, and the specific vulnerabilities detected. This allows for transparent security reporting, ensuring that all findings are traceable and verifiable. The SSCG serves as the formal security certification for analyzed components, ensuring that software artifacts meet RESCALE’s supply chain security standards.
Conclusion
The combination of SAVE-ME, SASTer, and IVEE within RESCALE’s Static Code Analysis Module represents a multi-layered approach to software security. By leveraging machine learning, rule-based analysis, and symbolic execution, RESCALE ensures that vulnerabilities are detected with high accuracy and low false positives.
Each of these tools plays a critical role in generating the SSCG, a structured security guarantee that contributes to a trusted and secure supply chain. As software security continues to evolve, the integration of advanced static analysis techniques will remain essential in safeguarding modern applications.