 Blog Post
Blog Post
The Silent Threat: Addressing Side-Channel Vulnerabilities in Software Supply…
Introduction
Supply chains form the backbone of modern industries, and their resilience is a cornerstone of operational security. While much of the discourse around supply chain vulnerabilities focuses on conventional cybersecurity risks, such as software vulnerabilities or malicious actors, side-channel vulnerabilities present an equally critical, yet often underestimated, threat. These vulnerabilities exploit indirect information leaks, such as timing, power consumption, or electromagnetic emissions, to infer sensitive data. The impact of such attacks on software and hardware supply chains can be devastating, leading to compromised components that cascade failures across dependent systems.
In this article, we delve into the nature of side-channel vulnerabilities in supply chains, examine their implications, and discuss emerging methodologies to mitigate these risks.
Understanding Side-Channel Vulnerabilities in Supply Chains
Side-channel attacks exploit unintended information channels that arise from the physical implementation of software or hardware components. Unlike direct attacks that target software flaws or network vulnerabilities, side-channel attacks leverage physical characteristics, such as:
- Timing Information: Differences in execution time for specific operations can reveal
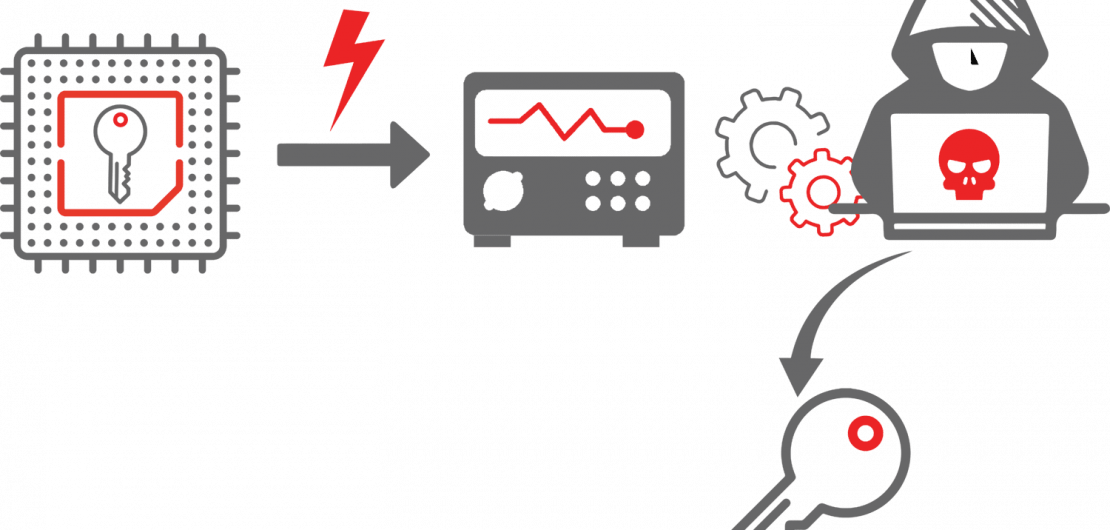
cryptographic keys. - Power Consumption Patterns: Variations in power usage during computations can be
correlated with specific data inputs. - Electromagnetic Emissions: Emanations from circuits can be intercepted and
analysed to extract sensitive information.
While side-channel vulnerabilities have traditionally been studied in the context of cryptographic systems, their impact on supply chains is equally profound. Components affected by these vulnerabilities can serve as entry points for attackers, compromising the integrity of the entire supply chain.
Examples of Side-Channel Vulnerabilities in Supply Chains
- Hardware Trojans: Introduced in Third-Party Manufacturing, many supply chains rely on external manufacturing facilities for hardware production. Malicious modifications to chip designs can introduce hardware Trojans, which can be exploited through side-channel techniques. For example, minor changes to circuit timing or power requirements can act as covert communication channels, enabling attackers to exfiltrate sensitive data.
- Software Libraries and Timing-Based Data Leaks: Third-party libraries integrated into critical software systems can inadvertently introduce timing vulnerabilities. For instance, a dependency library might handle sensitive data using non-constant time operations, allowing attackers to infer encryption keys or passwords.
- IoT Devices and Electromagnetic Emanations: The rise of IoT devices has exacerbated supply chain risks. Many IoT devices operate in environments where they can be physically accessed, making them susceptible to electromagnetic analysis. Inadequate shielding or poorly implemented security measures can make these devices prime targets for attackers seeking to compromise broader networks.
Mitigation Strategies for Side-Channel Risks
- Enhanced Static and Dynamic Analysis Tools: To detect side-channel vulnerabilities should be integrated into software development lifecycles and supply chain evaluation processes. Static code analysis and dynamic runtime testing can identify operations susceptible to timing or power-base attacks.
- Trusted Bill of Materials (TBOM): Adopting TBOM frameworks is critical for tracking the provenance and security posture of every component in the supply chain. Including side-channel resistance as a parameter in the TBOM can help ensure that components meet stringent security standards.
- Physical Security Measures for Hardware: Physical countermeasures, such as electromagnetic shielding, power line filtering, and secure enclaves, can mitigate side-channel risks for hardware components. Techniques such as randomised clocking or noise injection can further obscure exploitable patterns.
- Runtime Monitoring and Anomaly Detection: Integrating runtime monitoring systems focusing on side-channel-specific anomalies can detect potential exploitation attempts in real-time. Machine learning models trained on side-channel attack patterns can enhance the accuracy of these systems.
- Standardisation and Certification: Developing industry-wide standards for side-channel resistance is essential. Certification processes for hardware and software components should incorporate rigorous side- channel vulnerability assessments.
Conclusion
Side-channel vulnerabilities represent a critical yet underexplored dimension of supply chain security. The RESCALE project, emphasising secure-by-design supply chains, is uniquely positioned to address these risks. By integrating advanced analysis tools, fostering transparency through TBOM frameworks, and advocating for robust security standards, we can mitigate the cascading threats posed by side-channel attacks. The call to action is clear: organisations must prioritise side-channel resilience within their
supply chain strategies to safeguard the integrity and trust of their systems.